IT security starts with knowing your assets: Europe, the Middle East, and Africa
Cyberattacks know no geographical boundaries. In the past two years alone, the University Hospital Brno in the Czech Republic suffered a cyberattack during the covid-19 pandemic, forcing the medical facility to reroute patients and postpone surgery; South Africa’s major electricity supplier, City Power, fell victim to a ransomware attack, leaving many of Johannesburg’s residents without power; and Saudi Aramco, Saudi Arabia’s state oil giant, became the target of a cyber-extortion attempt.

Nations in Europe, the Middle East, and Africa are taking note: the European Commission plans to build a Joint Cyber Unit to tackle large-scale cyberattacks. The government of Saudi Arabia launched the National Cybersecurity Authority to enhance the country’s cybersecurity posture. And the African Union has identified cybersecurity as part of its Agenda 2063 for transforming Africa.
To explore the challenges facing today’s cybersecurity teams and the strategies they must embrace to protect the attack surface—the sum of points an unauthorized user can use to gain access to an organization’s systems— MIT Technology Review Insights and Palo Alto Networks conducted a survey of 728 business leaders. The survey was global, with 38% of respondents from Europe and 13% from the Middle East and Africa. Their responses, along with the input of industry experts, provide a solid framework for safeguarding against a growing battalion of bad actors and fast-moving threats.
But organizations themselves can also take critical steps to better understand where attacker entry points are in their information technology (IT) environments in a smart, data-driven manner.

The vulnerabilities of a cloud environment
The cloud continues to play a critical role in accelerating digital transformation. And for good reason: cloud offers solid benefits, such as increased flexibility, cost savings, and greater scalability. Yet cloud-based environments account for 79% of observed exposures, compared with 21% for on-premises assets, according to the “2021 Cortex Xpanse Attack Surface Threat Report.”
That’s concerning, given that 53% of survey respondents in Europe, and 48% of those in the Middle East and Africa, report that more than half of their assets are in the cloud.
“Many companies started their journey to the cloud because it made sense,” says Amitabh Singh, chief technology officer for Europe, the Middle East and Africa at Cortex, Palo Alto Networks’ security operations platform division. But there are pitfalls, too, he says.
“With the cloud, the high wall around organizations’ core assets and infrastructure has melted away. As a result, some of the assets companies thought were secure may be exposed to vulnerabilities.”
Certainly, there are technologies that can bolster cloud security. But Singh says many organizations in Europe have been slow to adopt more innovative tools. “I still see companies struggling with old antivirus and anti-malware platforms,” he says.
Remote work has also contributed to increasing cybersecurity risks for cloud environments. Remote workers rely on the cloud to do their jobs, whether it’s corresponding with co-workers, collaborating on projects, or getting on video conferencing calls with clients. And when IT, now at a physical remove, is not responsive to their needs, remote workers can easily shop for their own online solutions to problems. It’s what’s known as shadow IT: it bypasses normal cybersecurity practices—and opens up a world of worry for IT teams.
Just ask Chris Sandford, director of industrial cybersecurity services at Applied Risk, an industrial cybersecurity consultancy in the Netherlands. Sandford says while work-from-home arrangements have long been common in Northern Europe, “there are many companies that weren’t ready for remote work and its associated challenges and vulnerabilities” when the 2020 coronavirus pandemic forced many employees to work from home. Case in point: the majority (53%) of respondents in Europe, and 35% in the Middle East and Africa, say they have experienced a cybersecurity attack originating from an unknown, unmanaged, or poorly managed digital assets.
Sandford provides the hypothetical example of an employee who uses an unsecured cloud server to access business applications without the necessary authentication or authorization measures in place. “How do you know someone’s not backtracking from that cloud back into your own network?” he asks. “There’s very limited visibility or understanding of that cloud service.”
A powerful action plan
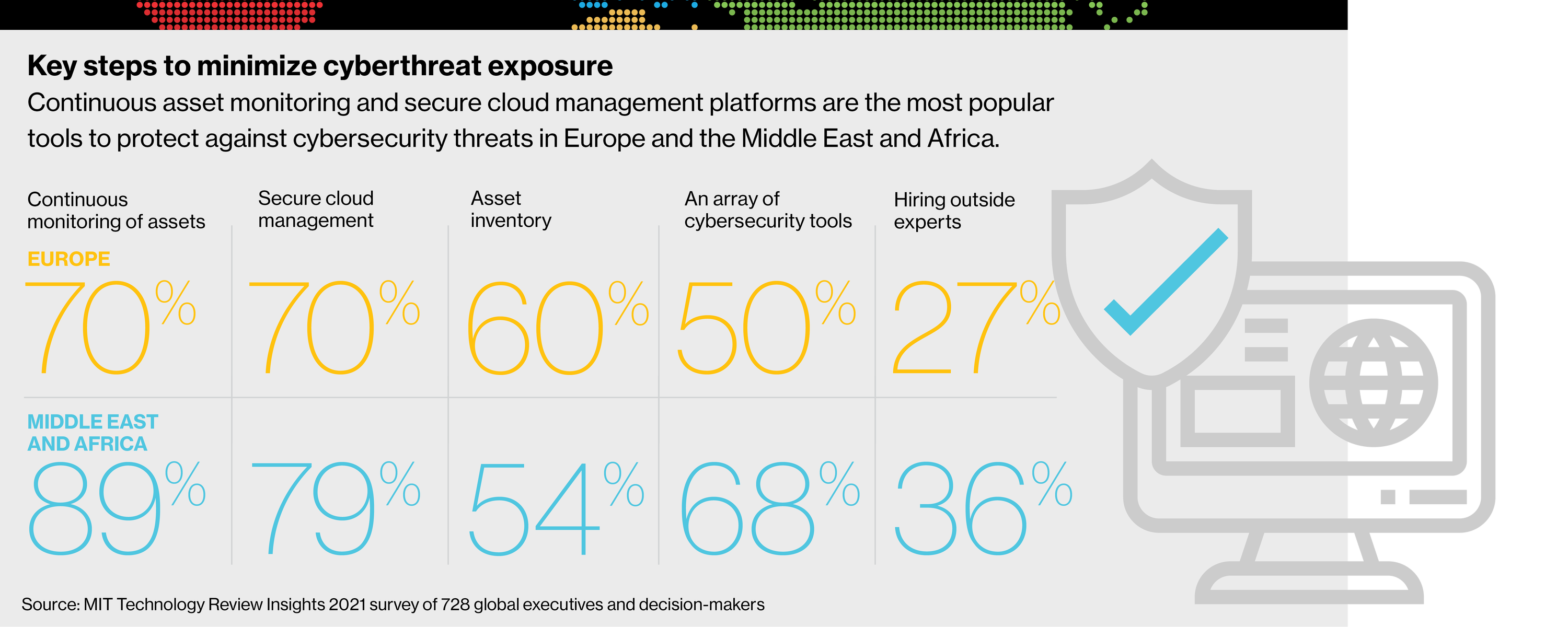
Fortunately, there are steps organizations in Europe, the Middle East, and Africa can take to minimize exposure to cybersecurity threats and gain control of their cloud environments. Most survey respondents in Europe (70%) and the Middle East and Africa (89%) rely on continuous asset monitoring technology for protection. Long gone are the days when companies could take an ad hoc approach to identifying security risks.
“In the good old days, when we were managing vulnerabilities, we used to scan our infrastructure on a regular basis, find the vulnerabilities, and then patch them,” says Singh. “Now, we don’t have the luxury of time. If there are vulnerabilities, and we don’t manage them almost on an instantaneous basis, bad actors can exploit them.”
Download the full report.
This content was produced by Insights, the custom content arm of MIT Technology Review. It was not written by MIT Technology Review’s editorial staff.

