A game changer in IT security
The key to a successful cybersecurity strategy is knowing what you need to protect. Here’s the proof: half of companies surveyed by MIT Technology Review Insights and Palo Alto Networks have experienced a cyberattack originally from an unknown, unmanaged, or poorly managed digital asset, and another 19% expect to experience one eventually.

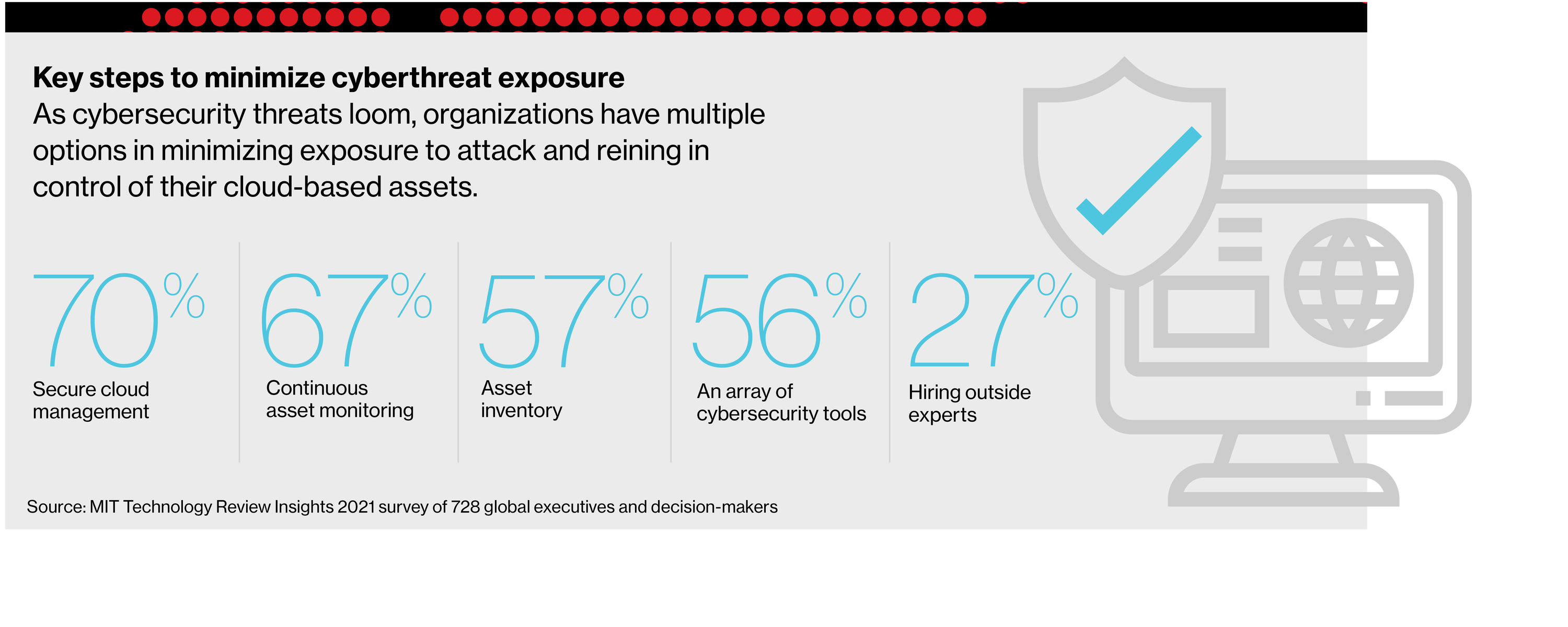
Without a full inventory of internet-connected assets, organizations simply can’t identify and remediate exposures to cyberattacks. Yet only half of companies surveyed ensure continual monitoring of assets, and just slightly more (57%) cite asset inventory as a critical precautionary measure.
The clock is ticking: while Fortune 500 companies find one serious vulnerability every 12 hours, it takes attackers less than 45 minutes to do the same as they scan the vastness of the internet for vulnerable business assets.
Making matters worse, bad actors are multiplying, highly skilled IT professionals are a scarce resource, and the demand for contactless interactions, remote work arrangements, and agile business processes continues to expand cloud environments. This all puts an organization’s attack surface—the sum total of the nooks and crannies hackers can pry into—at risk.
“We’ve seen a pretty steady set of attacks on different sectors, such as health care, transportation, food supply, and shipping,” says Gene Spafford, a professor of computer science at Purdue University. “As each of these has occurred, cybersecurity awareness has risen. People don’t see themselves as victims until something happens to them—that’s a problem. It’s not being taken seriously enough as a long-term systemic threat.”
Organizations must understand where the critical entry points are in their information technology (IT) environments and how they can reduce their attack surface area in a smart, data-driven manner. Digital assets aren’t the only items at risk. An organization’s business reputation, customer allegiance, and financial stability all hang in the balance of a company’s cybersecurity posture.
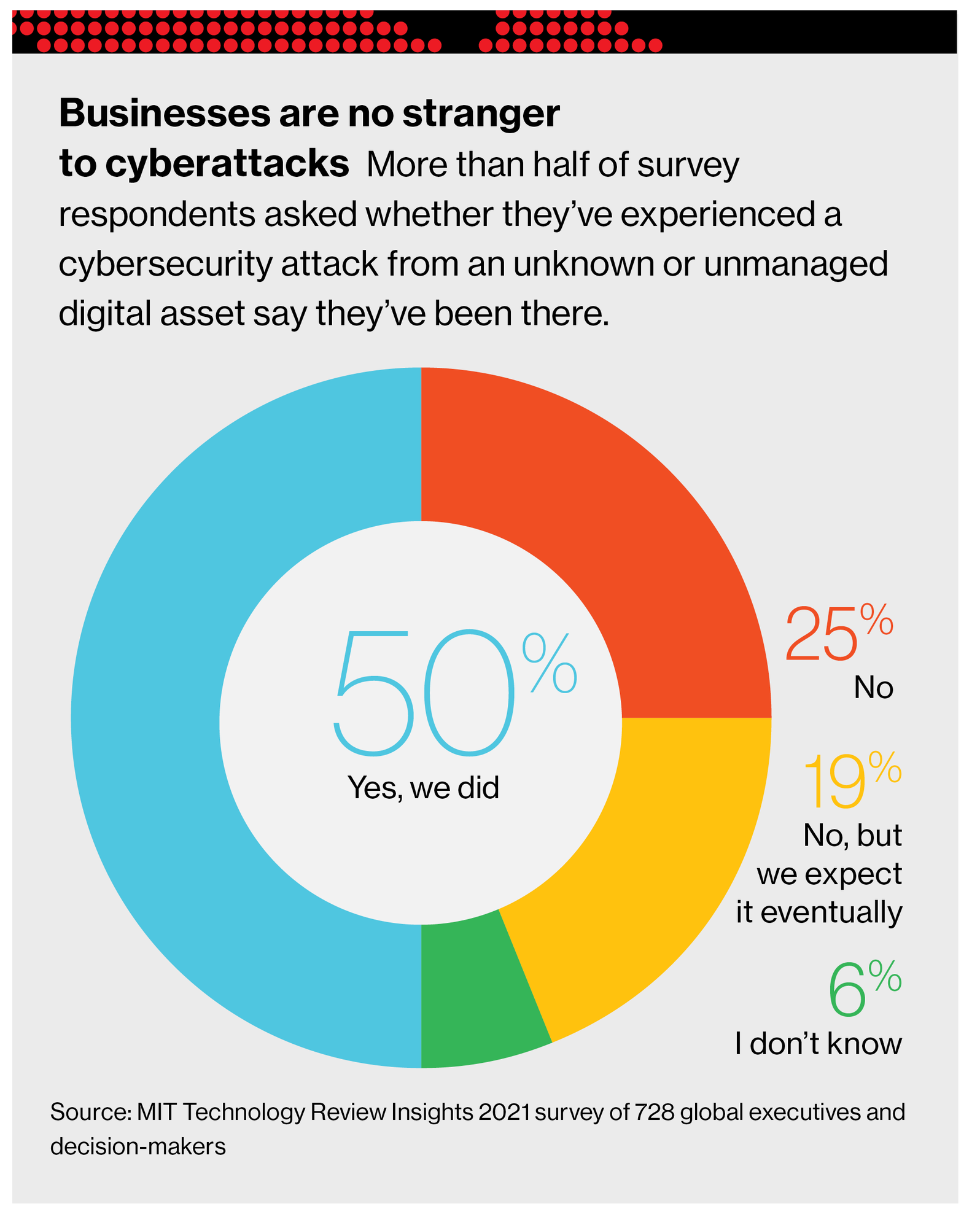
To better understand the challenges facing today’s security teams and the strategies they must embrace to protect their companies, MIT Technology Review Insights and Palo Alto conducted a global survey of 728 business leaders. Their responses, along with the input of industry experts, provide a critical framework for safeguarding systems against a growing battalion of bad actors and fast-moving threats.
The vulnerabilities of a cloud environment
The cloud continues to play a critical role in accelerating digital transformation—and for good reason: cloud offers substantial benefits, including increased flexibility, huge cost savings, and greater scalability. Yet cloud-based issues comprise 79% of observed exposures compared with 21% for on-premises assets, according to the “2021 Cortex Xpanse Attack Surface Threat Report.”
“The cloud is really just another company’s computer and storage resources,” says Richard Forno, director of the graduate cybersecurity program at the University of Maryland, Baltimore County. “Right there, that presents security and privacy concerns to companies of all sizes.”
Even more concerning is this: 49% of survey respondents report more than half of their assets will be in the public cloud in 2021. “Ninety-five percent of our business applications are in the cloud, including CRM, Salesforce, and NetSuite,” says Noam Lang, senior director of information security at Imperva, a cybersecurity software company, referring to popular subscription-based applications handling customer relationship management. But while “the cloud provides much more flexibility and easy growth,” Lang adds, “it also creates a huge security challenge.”
Part of the problem is the unprecedented speed at which IT teams can spin up cloud servers. “The cadence that we’re working at in the cloud makes it much more challenging, from a security perspective, to keep track of all of the security upgrades that are required,” says Lang.
For example, Lang says, in the past, deploying on-premises servers entailed time-consuming tasks, including a lengthy buying process, deployment activities, and configuring firewalls. “Just imagine how much time that allowed our security teams to prepare for new servers,” he says. “From the moment we decided to increase our infrastructure, it would take weeks or months before we actually implemented any servers. But in today’s cloud environment, it only takes five minutes of changing code. This allows us to move the business much more quickly, but it also introduces new risks.”
Download the full report.
This content was produced by Insights, the custom content arm of MIT Technology Review. It was not written by MIT Technology Review’s editorial staff.

